How VPN Works? Behind the Scenes of Security!
- March 5, 2024
- 11 minutes Read
- Security & Privacy
When you connect to a VPN, it encrypts your network and changes your original IP address to a virtual IP address. This allows you to browse the internet securely without the feat of cyber attacks, hacks, or surveillance.
In this guide, we’ll take you behind the scenes of how a VPN works to protect your digital life. It’s like having a personal bodyguard for your data. Let’s dive into the world of online security and see how a VPN keeps your secrets safe.
Table of contents
What is a VPN?
Think of a regular internet connection as an open road. Anyone can see where you’re going and what you’re carrying. A VPN, or Virtual Private Network, is like a secret tunnel for your internet traffic. It encrypts your data, making it unreadable, and hides your online activity, keeping it private and secure.
Additionally, VPNs can help you unblock any sites anywhere securely and anonymously. As a result, you can stream your favorite shows anytime, anywhere in the world. Almost every individual and business is currently using a VPN in 2024 for digital security.
If you’re curious about the different roles within a VPN network, you can learn about the difference between VPN server vs client vs bridge.
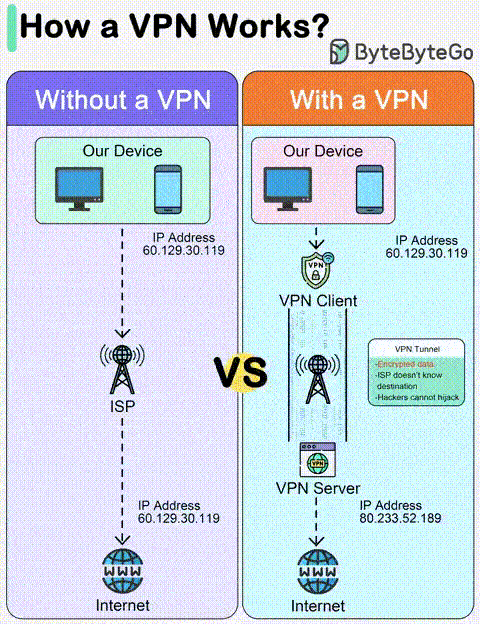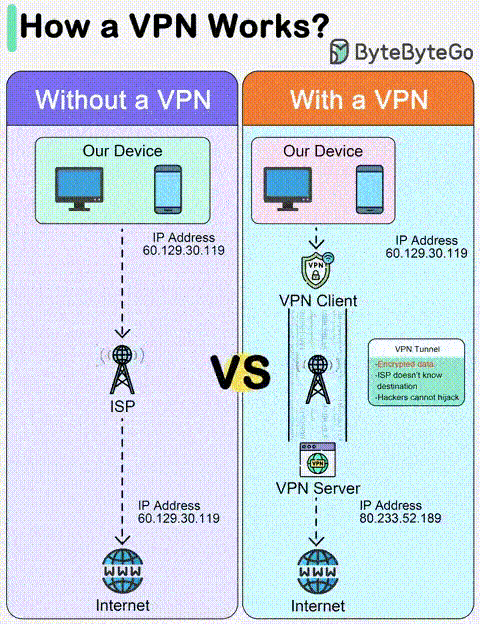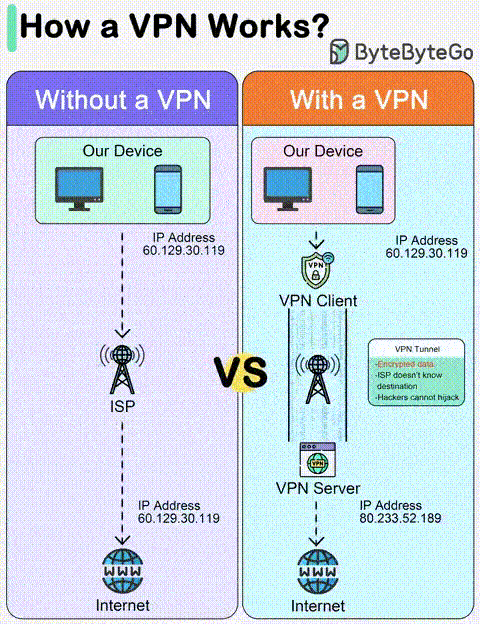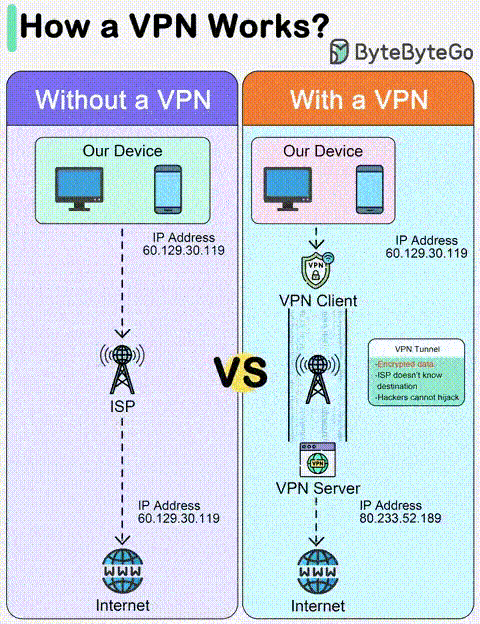
Credit: @bytebytego
There are people who say, “I have nothing to hide; why should I use a VPN?”. Even though you don’t have anything to hide, you may need to use a Virtual Private Network.
- Safer Public Wi-Fi: Public Wi-Fi at cafes or airports can be risky. There are reports of people getting hacked on public Wi-Fi. A VPN protects your information from all cyber threats and prying eyes.
- Privacy Boost: Don’t want websites tracking your every move? A VPN hides your location and browsing activity from your ISP and government, turning you completely anonymous online.
- No Restriction: Some websites are blocked in certain countries due to copyright, censorship, and regional restrictions. A VPN can help you access them by making it seem like you’re somewhere else.
- Secure Streaming & Gaming: Enjoy smooth streaming and lag-free gaming with a VPN’s faster speeds and better security.
How Do VPN Servers Work?
Now, let’s get Technical, shall we? We’ll dig deeper into the algorithmic level to find out how VPN servers work to secure your connection when you tap on “Connect.”
Virtual Private Networks (VPNs) operate through a complex interplay of cryptography, tunneling protocols, and server-side infrastructure.
At its core, a VPN server acts as a secure intermediary between your device and the wider internet. When you establish a VPN connection, your device initiates a handshake with the chosen server, utilizing protocols like WireGuard, OpenVPN, or Shadowsocks.
This creates a tunneled connection, encapsulating your data within a layer of encryption, typically AES-256 or ChaCha20Poly1305.
The encryption standard and networking protocol (TCP/UDP) may vary depending on the VPN protocol. It’s like an encrypted tunnel protecting your data from outer threats.
Once the tunnel is established, your device routes all its internet traffic through the VPN server. This traffic traverses over your regular internet connection to reach the server, but once there, it undergoes decryption and further processing.
The server then forwards the decrypted data to its intended destination on the internet, acting as your masked envoy.
However, the server itself plays a crucial role in ensuring VPN functionality and security. Let’s dissect its key components:
- Virtual Interfaces: The server utilizes virtual network interfaces (VNIs) to manage separate encrypted tunnels for each connected client. This segregation ensures privacy and prevents data leakage between users.
- Routing Infrastructure: The server employs sophisticated routing protocols to direct traffic towards its final destination efficiently. This involves selecting optimal paths, managing congestion, and ensuring latency remains low.
- NAT (Network Address Translation): The server often employs Network Address Translation (NAT) to obfuscate your original IP address. This assigns a temporary IP address from the server’s pool, further enhancing your anonymity.
- DNS Resolution: Secure DNS resolution is crucial for ensuring your online activities remain untraceable. VPN servers may offer their own encrypted DNS resolvers to prevent leaks and maintain privacy.
- Logging Policies: Transparency is paramount when it comes to data logging. Reputable VPN providers adhere to strict no-logging policies, ensuring your online activity remains unmonitored and untracked.
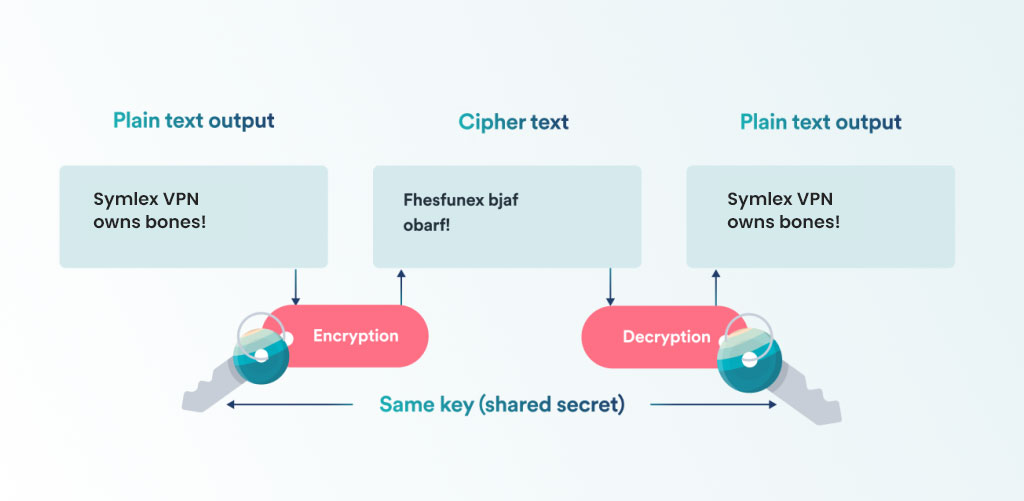
How Does a VPN Server Encryption Work?
Now, let’s get deeper insights into how vpn server encryption works.
Step 1: VPN Client Initialization
The process begins when you launch the VPN client on your device. This software is responsible for managing your connection to the VPN server. When you tap on the connect button, it attempts to establish a connection with the VPN server.
Step 2: Secure Connection Establishment
The VPN client contacts the VPN server, requesting a secure connection. This involves the exchange of encryption keys and the establishment of a secure tunnel protocol (like OpenVPN, IKEv2/IPSec, or L2TP/IPSec) through which all internet traffic will be routed.
Note: Encryption standards will vary depending on the type of protocol.
Step 3: Authentication
Then you need to authenticate yourself to the VPN server, often using a username and password, digital certificates, or two-factor authentication. This step ensures that only authorized users can access the VPN service.
Step 4: Encryption
Once authenticated, all data transmitted between your device and the VPN server is encrypted. The data is transformed into a ciphertext using strong encryption algorithms, rendering it unreadable without the specific decryption key.
This encryption protects your data from being intercepted and read by unauthorized parties. One of the most popular and strongest encryption is the AES-256 bit standard.
Step 5: Data Transmission
Once the secure tunnel is established, the VPN server routes your internet traffic. To any observer outside, like your internet provider or hackers, your traffic seems like a single stream of encrypted data. This makes your online activities private and secure.
Step 6: IP Address Masking
The VPN server masks your real IP address with a virtual IP. This means that any website or online service you access sees the VPN server’s IP address instead of your original IP. This keeps your location and info private and lets you bypass geo-blocks and censorship.
Step 7: Secure Data Arrival
Your encrypted data reaches its destination via the VPN server. The receiving server (e.g., a website) sees the data as coming from the VPN server’s IP address, not from your original location or IP securing your online anonymity.
Step 8: Decryption and Response
The encrypted data is decrypted at the destination point if it’s meant for a server outside the VPN network or at your device if it’s incoming data. The process ensures that your data remains confidential and secure throughout its journey.
Step 9: Continuous Security Checks
Throughout the session, the VPN software continuously checks the integrity and security of the connection. If any unauthorized attempts to breach the connection are detected, the VPN can automatically disconnect or re-establish a secure connection. This security feature is known as Kill Switch that prevents IP leaks.
Does VPN use TCP or UDP?
VPNs use both TCP and UDP but these two network protocols may vary based on the different VPN tunneling protocols & VPN service provider.
Here’s a brief comparison table on TCP vs UDP.
| Feature | TCP | UDP |
| Speed | Slower | Faster |
| Reliability | More reliable (guaranteed delivery) | Less reliable (possible packet loss) |
| Efficiency | Less efficient (more overhead) | More efficient (less overhead) |
| Firewalls | Might be blocked by some firewalls | Less likely to be blocked |
What is the Best Protocol?
VPNs use multiple protocols like WireGuard, OpenVPN, IKEv2/IPSec, L2TP/IPSec, PPTP, Shadowsocks, OpenConnect, etc. Some of them are good for sensitive tasks like sending email, texting and some protocols are best for gaming and streaming.
| Protocols | Encryption | Authentication | Key Features | Best for? |
| OpenVPN | AES-256 ChaCha20,Poly1305 | Various (TLS, HMAC) | Open source, highly customizable, strong security | Overall Security & Privacy |
| IKEv2/IPSec | AES-256, Blowfish | EAP (e.g., TLS, PSK) | Mobile-friendly, fast reconnection, good balance of security and speed | Mobile Devices & Frequent Disconnects |
| WireGuard | Noise protocol framework, Curve25519,ChaCha20 | Noise protocol | Lightweight, simple, ultra-fast, emerging standard | Speed & Performance (limited server availability) |
| L2TP/IPSec | AES-256, DES | Various (e.g., PSK, X.509 certificates) | Widely supported, compatible with older devices | Basic Security & Compatibility (potentially slower) |
| PPTP | DES, RC2 (obsolete) | PAP, CHAP (insecure) | Easy to set up, very fast, but outdated and insecure | Not recommended for security-sensitive use |
How to Choose a Good VPN?
Now comes a challenging question! How can you choose a VPN that’s good for you? Well, you need to consider some important factors:
- Why do you need a VPN?
- How often do you use a VPN?
- What’s your budget on using a VPN?
Don’t be lost, we’ve done the study for you, here are the features your chosen VPN service should have to meet your every VPN needs:
- Strong Security: Most popular VPNs use strong encryption standard, AES-256 bit encryption. If the VPN offers such encryption you are in safe hands!
- Faster Speed: Speed is crucial in terms of VPNs. Many VPNs compromise speed at the sake of providing good security. Ensure you choose a VPN that combines both speed and security.
- No-logging Policy: No one wants their activities to be logged right? Some VPN providers sell user data to advertisers or AI companies for research, process, and target marketing. The VPN you choose should offer a no-logging policy.
- Large Server Collection: VPNs must have a wide collection of servers to meet your gaming and streaming needs. Some TV-shows and games are geo-blocked, which can only be unlocked in certain countries.
- Unlimited Bandwidth: Limited bandwidth is the main issue of many VPNs like TunnelBear, Privado VPN, Hotspot Shield. Choose a VPN that comes with unlimited bandwidth like Symlex VPN. There are free options available but limited like ProtonVPN.
- Customer Support: Having good customer support is a must. Your payment may fail, the server may slow down, anything can happen. A good customer service ensures they care about their customers.
If you’re curious about the advantages of using a VPN for secure downloading, check out our detailed guide on the best VPN for downloading torrents. This comprehensive article explains how VPNs can enhance your privacy and security while torrenting, ensuring a safer online experience.
Free vs Paid VPN
Free VPNs are like digging your own grave, once you connect you don’t know what happens to your data. Here’s a brief comparison on free vs paid VPN.
| Feature | Free VPN | Paid VPN |
| Cost | Free | Paid subscription (monthly, yearly) |
| Data Limits | Often capped, sometimes very low | Usually, unlimited or high limits |
| Speed | Can be slow, especially during peak hours | Typically much faster, good for streaming & gaming |
| Server Locations | Few server options, limited choice | Many server locations, global access |
| Security | Can be less secure, and data logging is possible | Strong encryption, no data logging |
| Privacy | May sell your data or inject ads | Protects your privacy, focuses on anonymity |
| Device Connections | Often limited to 1 device | Allows multiple devices simultaneously |
| Customer Support | Limited or no support | 24/7 live chat and email support |
| Technical Features | Basic features, limited customization | Advanced features, protocols like WireGuard |
| Ease of Use | Usually simple interface | Some technical knowledge may be needed |
| Best for | Occasional, low-bandwidth use | Regular internet use, streaming, security & privacy |
Privacy Policy and Trust
You entrust your online identity and activities to your VPN provider. Choosing the right one becomes crucial, and trust plays a significant role. Here’s why:
1. Your Data, Their Responsibility: Your VPN handles sensitive information like browsing history, IP address, and sometimes even login credentials. A clear and concise privacy policy outlines how they collect, use, and store this data.
2. No Logs, No Worries: We’ve been screaming about this! Look for providers with a strict “no-logs” policy. This means they don’t track your online activity, ensuring maximum privacy and protection from prying eyes.
3. Transparency is Key: A good privacy policy is easy to understand, avoiding technical jargon and hidden clauses. It should answer key questions like:
- What data do they collect?
- How is it used and shared?
- What security measures are in place?
- What happens to your data when you cancel?
4. Independent Audit: Choos VPN that are independently audited by experts, check whitepapers. Audits prove that the services they provide are legit and trustworthy.
By following the advice, you can choose the perfect VPN for your business or family.
Closing Thoughts
VPNs are a great tool for protecting your online security in a world where threats lurk around all over the web. In a blink of an eye, you can lose all your money from your credit card if you are serious about the cyber threats.
You must have watched the movie named “ The Beekeeper” where a senior citizen gets hacked by cyber criminals. Imagine yourself in that situation! That can be absolutely devastating. It’s high time you should be concerned about your digital security.
Symlex VPN can be your 360-degree digital security co-pilot. Give it a try!
![Ultimate White Label VPN Business Guide 2026 [Cost & ROI]](https://symlexvpn.com/wp-content/uploads/2026/01/Ultimate-White-Label-VPN-Business-Guide-2025-Cost-ROI_2-376x114.webp)