Must-Have Security Protocols for a Modern VPN App [2025]
- May 21, 2025
- 12 minutes Read
- Security & Privacy
Imagine using the internet in 2025.
You click, you browse, you connect – but who’s watching?
In a world where your online activity is constantly watched and access to information can be blocked at any time, your Virtual Private Network (VPN) is your solution. But the real power is in the way it works behind the scenes: the security protocols.
Think of it as the secret language your VPN uses to keep your data secure and your connection open. From the reliable WireGuard to the innovative Trojan and V2Ray protocols, these technologies are becoming more accessible to everyone.
It’s your way to be free online again. This guide uses simple language to explain the most important VPN protocols that will be important in 2025. This will help you to choose a solution that offers real privacy and lets you access anything you want online.
Table of contents
- Understanding VPN Protocols
- Essential Protocols for Modern VPN Applications
- Advanced Protocols for Bypassing Censorship and Geo-Blocking
- Comparison: Traditional VPN Protocols vs. Censorship Circumvention Protocols
- Proprietary Protocol Innovations Worth Considering
- Critical Security Components Beyond Protocols
- Protocols to Categorically Avoid ❌
- Implementation Best Practices for VPN Providers
- Honorary Mentions: Special Censorship Bypass Protocols
- Future-Proofing: Emerging Protocol Considerations
- The Right Protocol for Your Needs
- Why Choose Symlex VPN as Your VPN Business Partner
- Ready to Launch Your VPN Business?
Understanding VPN Protocols
A VPN protocol is essentially the set of instructions and encryption standards that govern how your data travels between your device and the VPN server.
Imagine it as data packet armor and a navigation system combined, enhancing both security and network efficiency. The protocol you use directly impacts:
- Security: The strength of encryption and resistance to attacks
- Speed: How efficiently data packets are processed and routed
- Stability: Reliability during network transitions and under adverse conditions
- Compatibility: Which devices and operating systems can use the VPN
- Censorship resistance: Ability to bypass government firewalls and content restrictions.
Essential Protocols for Modern VPN Applications
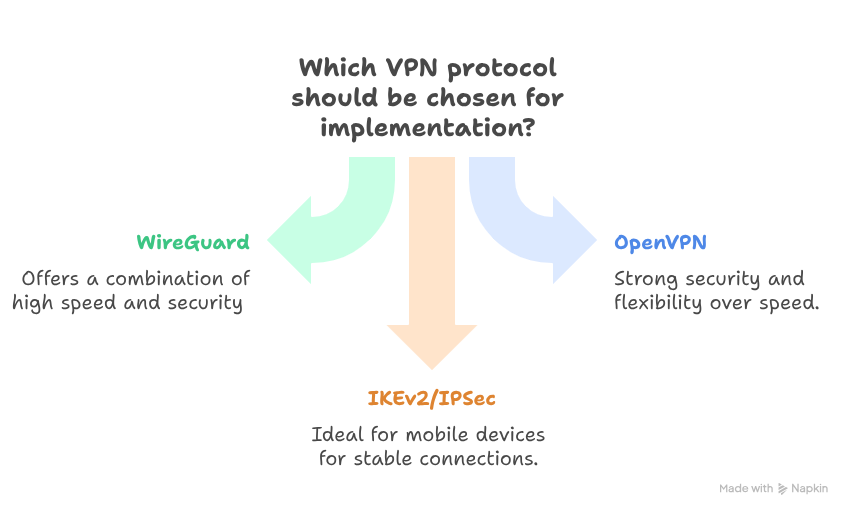
WireGuard: The Allrounder on Speed & Security
WireGuard has revolutionized the VPN landscape since its introduction. Its remarkably lean codebase, approximately 4,000 lines compared to OpenVPN’s 400,000+, creates an inherently smaller attack surface for potential vulnerabilities.
Technical specifications:
- Encryption: ChaCha20 for symmetric encryption, Poly1305 for authentication
- Cryptographic primitives: Curve25519 for key exchange, BLAKE2s for hashing
- Transport: UDP-only implementation for speed optimization
- Key exchange: Noise Protocol Framework with handshake pattern Noise_IK
WireGuard’s technical architecture allows it to achieve connection speeds up to 4x faster than OpenVPN while maintaining exceptional security.
The cryptographic approach, simplified to use only the most secure algorithms, eliminates legacy options, preventing misconfiguration.
OpenVPN: When Security Matters than Speed
Despite newer alternatives, OpenVPN remains essential for any comprehensive VPN implementation due to its unmatched flexibility and proven security track record.
Technical specifications:
- Encryption: AES-256-GCM (Galois/Counter Mode) for authenticated encryption
- Authentication: HMAC SHA-256 hash authentication
- Key exchange: TLS with ephemeral Diffie-Hellman or elliptic curve variants
- Transport: Both TCP and UDP support on multiple ports.
- Perfect Forward Secrecy: Implemented through TLS key renegotiation
OpenVPN’s strength lies in its adaptability; it can be configured to prioritize security, speed, or obfuscation depending on user needs.
Its open-source nature ensures continuous security improvements through community review, making it particularly valuable for high-security environments.
IKEv2/IPSec: IIdeal for Mobile Devices
For VPNs targeting mobile users, IKEv2/IPSec offers exceptional stability during network transitions through its MOBIKE (Mobility and Multihoming) support.
Technical specifications:
- Encryption: AES-256 in CBC or GCM modes
- Authentication: SHA-2 family hash functions
- Key exchange: Diffie-Hellman groups 14+ or elliptic curve groups
- Transport: UDP on port 500 (IKE) and 4500 (NAT-T)
- Connection resilience: MOBIKE extension for maintaining connections during network switches
IKEv2/IPSec excels at rapid tunnel reestablishment when connections are temporarily lost, crucial for mobile users moving between Wi-Fi and cellular networks. Its integration into modern operating systems also makes it more battery-efficient than alternatives.
Advanced Protocols for Bypassing Censorship and Geo-Blocking
While traditional VPN protocols offer excellent security for most users, environments with strict internet censorship require specialized solutions.
Trojan and V2Ray protocols have emerged as leading technologies for circumventing even the most sophisticated censorship systems.
Trojan Protocol: The Trojan Horse of Troy 🐴
IT has become a go-to solution for users in heavily restricted internet environments due to its sophisticated camouflage capabilities.
Technical and operational features:
- HTTPS Masquerading: Routes encrypted traffic through port 443 (standard HTTPS port), making Trojan traffic blend with regular secure web browsing and difficult for censors to detect.
- Genuine TLS Handshakes: Performs authentic TLS connections that appear legitimate to monitoring systems, with SHA224-based password verification.
- Smart Fallback System: Failed authentication attempts redirect to normal websites, effectively hiding the proxy’s existence from active probing.
- DPI-Resistant Design: Mimics standard web browsing patterns to bypass even sophisticated Deep Packet Inspection systems used by restrictive governments.
- Distributed Server Network: Operates across multiple jurisdictions to prevent single-point blocking and ensure continuous availability.
V2Ray Protocol: The Versatile Multi-Protocol Framework 🛡️
V2Ray offers exceptional flexibility and adaptability for circumventing censorship through its multi-protocol support and advanced configuration options.
Technical and operational features:
- Protocol Versatility: Supports multiple protocols (VMess, Trojan) with customizable obfuscation that can mimic regular web traffic or utilize WebSocket over TLS to evade detection.
- Geo-location Flexibility: Routes connections through diverse server locations, enabling users to bypass regional content restrictions by appearing to browse from different countries.
- Dynamic Security Model: Implements rotating session keys and varied encryption methods that create unique connections, effectively preventing eavesdropping and replay attacks.
- Optimized Performance: Features advanced traffic management and efficient routing to maintain speed and stability even on heavily restricted networks.
Comparison: Traditional VPN Protocols vs. Censorship Circumvention Protocols
Here’s a quick comparison on traditional VPN protocols vs Special VPN protocols.
| Features | Traditional VPNs (WireGuard, OpenVPN) | Censorship Circumvention (Trojan, V2Ray) |
| Primary Purpose | General security and privacy | Bypassing censorship and geo-blocks |
| Traffic Fingerprinting | Can be identified as VPN traffic | Nearly indistinguishable from normal traffic |
| Deep Packet Inspection (DPI) Resistance | Moderate | Very high |
| Configurability | Limited to moderate | Highly configurable |
| Server Infrastructure | Centralized VPN servers | Often decentralized, distributed architecture |
| Ideal Use Case | Everyday privacy and security | Accessing content in heavily censored regions |
Proprietary Protocol Innovations Worth Considering
Lightway (ExpressVPN)
This proprietary protocol combines WireGuard’s speed with enhanced security features:
- Built on wolfSSL cryptographic library (FIPS 140-2 validated)
- Supports both UDP and TCP transports for versatility
- Implements post-quantum cryptography through Kyber-1024 algorithms
- Lightweight design optimized for mobile performance
NordLynx (NordVPN)
NordLynx builds on WireGuard’s foundation while addressing privacy concerns:
- IEliminates identifiable user data storage by implementing a double NAT system.
- Maintains WireGuard’s performance advantages while enhancing privacy
- Optimizes routing algorithms for reduced latency
Critical Security Components Beyond Protocols
While protocols form the foundation, modern VPNs require additional security layers:
Perfect Forward Secrecy (PFS)
PFS ensures that if an encryption key is compromised, it cannot be used to decrypt past sessions. Modern implementations generate unique session keys through ephemeral Diffie-Hellman key exchanges, isolating the security impact of any potential breach.
Advanced Authentication Mechanisms
Modern VPNs should employ multiple authentication layers:
- Certificate-based authentication: Using X.509 certificates for mutual authentication between client and server
- Multi-factor authentication: Requiring additional verification beyond passwords
- Public key infrastructure (PKI): Managing digital certificates and public-key encryption
Protocols to Categorically Avoid ❌
PPTP (Point-to-Point Tunneling Protocol)
Despite its continued presence in some applications, PPTP is fundamentally broken:
- Uses compromised MS-CHAPv2 authentication vulnerable to brute-force attacks
- Implements RC4 stream cipher with known weaknesses
- Has been crackable since 2012 using readily available tools
L2TP/IPSec with Pre-Shared Keys
When implemented with pre-shared keys rather than certificates:
- Vulnerable to offline dictionary attacks against weak pre-shared keys
- Potentially compromised by intelligence agencies according to leaked documents
- Offers no significant advantages over more secure alternatives
Implementation Best Practices for VPN Providers
Protocol Diversification
Modern VPN applications should support multiple protocols, implementing:
- WireGuard as the primary protocol for optimal performance
- OpenVPN for maximum compatibility and high-security environments
- IKEv2/IPSec for mobile-optimized connections
- Trojan or V2Ray for users in heavily censored regions
Automatic Protocol Selection
Implement intelligent defaults that select the optimal protocol based on:
- Network conditions (detection of restrictive firewalls or deep packet inspection)
- Device capabilities (hardware acceleration availability)
- Connection priorities (security vs. speed preferences)
- User location (automatically switching to censorship-resistant protocols when needed)
Performance Optimization Techniques
- MTU optimization: Setting appropriate Maximum Transmission Unit sizes to prevent fragmentation
- Hardware acceleration: Leveraging AES-NI instructions for enhanced encryption performance
- QoS implementation: Prioritizing VPN control packets to maintain connection stability
Honorary Mentions: Special Censorship Bypass Protocols
While Trojan and V2Ray have gained significant popularity for bypassing censorship, several other protocols deserve recognition for their contributions to internet freedom.
Shadowsocks: The Pioneer of Modern Circumvention
Originally developed in 2012 to bypass the Great Firewall of China, Shadowsocks pioneered many techniques now common in anti-censorship tools.
Key attributes:
- SOCKS5 Proxy Implementation: Shadowsocks functions as a SOCKS5 proxy with added encryption layers, making it versatile for various applications.
- Pluggable Transport System: Supports plugin architecture for additional obfuscation methods like simple-obfs and v2ray-plugin.
- Customizable Encryption: Offers multiple encryption options including AES, ChaCha20, and Salsa20 ciphers.
- Lightweight Design: Minimal resource usage makes it ideal for deployment on low-powered devices.
Shadowsocks remain widely used due to its simplicity, efficiency, and continued development by the open-source community. Its influence on subsequent protocols, including Trojan and V2Ray, is significant.
Psiphon: The Resilient Multi-Protocol Solution
Developed with support from the University of Toronto’s Citizen Lab, Psiphon combines multiple circumvention techniques into one comprehensive solution.
Key attributes:
- Protocol Diversity: Automatically switches between SSH+, obfuscated SSH, WebSocket, and more based on network conditions.
- Robust Server Infrastructure: Utilizes a constantly changing network of servers that are difficult to block entirely.
- Integrated Obfuscation: Employs domain fronting and other techniques to mask traffic patterns.
- User-Friendly Design: Prioritizes accessibility for non-technical users in censored environments.
Psiphon’s strength lies in its adaptability, when one connection method fails, it seamlessly transitions to others without user intervention. This resilience makes it particularly effective in environments where censorship techniques evolve rapidly.
Future-Proofing: Emerging Protocol Considerations
As quantum computing advances threaten current cryptographic standards, forward-looking VPNs should:
- Implement hybrid post-quantum cryptographic schemes alongside traditional algorithms
- Support regular cryptographic agility to quickly deploy algorithm updates
- Maintain modular protocol implementations to adapt to emerging threats
- Continue developing enhanced obfuscation techniques to counter evolving censorship technologies
The Right Protocol for Your Needs
By 2025, the ideal VPN solution depends heavily on individual requirements:
- For general users in open internet environments, WireGuard and modern proprietary protocols offer the best balance of security and performance.
- For mobile users with frequently changing networks, IKEv2/IPSec provides superior stability.
- For users in countries with strict internet censorship or those needing to bypass geo-blocking, Trojan and V2Ray protocols offer unparalleled capabilities for disguising traffic and maintaining access to restricted content.
As the digital privacy landscape continues to change, understanding these rules is no longer optional, it’s essential for protecting your privacy and freedom online.
Why Choose Symlex VPN as Your VPN Business Partner
Looking to enter the thriving VPN market but not sure where to start?
Collaborating with Symlex VPN offers you the fastest and most cost-effective path to launching your own branded VPN service in 2025.
Symlex VPN stands out as a global provider renowned for censorship bypass and data security, offering two powerful options to enter the VPN market:
White Label VPN Solution: Your Fastest Path to Market
The white label VPN option is ideal if you want to launch quickly with low investment:
- Fully customized branding – Your logo, colors, and identity on a proven VPN platform
- Complete admin panel – Manage users, monitor performance, and analyze business metrics
- Ready-made server infrastructure – No need to invest in expensive hardware or bandwidth
- Payment gateway integration – Start collecting subscription revenue immediately
- Next-generation security features – Military-grade encryption and privacy protection
With Symlex’s white label solution, you can have your branded VPN ready for customers in weeks rather than months, at a fraction of the development cost.
This option eliminates server infrastructure costs, bandwidth acquisition costs, and business licensing fees – dramatically reducing your startup expenses.
Custom VPN App Development: Your Unique VPN Vision
If you have specific requirements or a unique VPN concept, Symlex VPN’s custom VPN app development services deliver:
- Tailor-made applications across all major platforms (Windows, Android, macOS, Chrome extensions)
- Distinctive features that set your VPN apart from competitors
- Complete ownership of your proprietary technology
- Specialized targeting for specific market niches (gamers, businesses, privacy enthusiasts)
Custom development costs between $500-$2,500 per platform but gives you complete control over your product’s direction and features*
Which Option Is Right For You?
Choose White Label if:
- You want to enter the market quickly
- Your startup budget is limited
- You need a proven, reliable VPN solution immediately
- You’re focused on marketing and growing your customer base
Choose Custom Development if:
- You have a unique VPN concept
- You’re targeting a specific niche market
- You want complete control over your technology
- You need specialized features not available in standard solutions
The Market Opportunity Is Now!
With the global VPN market projected to reach $534.22 billion by 2034 (growing at 22.04% annually), and cybersecurity threats driving adoption, entering the VPN business now positions you perfectly for substantial growth.
Ready to Launch Your VPN Business?
Contact Symlex VPN today to discuss which solution best fits your business goals.
Our team of experts will guide you through the process, ensuring you make the most profitable choice for your specific situation and demand.
Contact us here: https://wa.me/18454009402
Don’t miss the opportunity to join one of the fastest-growing sectors in digital security with a partner who handles all the technical complexity while you focus on building your brand and growing your customer base.
![Ultimate White Label VPN Business Guide 2026 [Cost & ROI]](https://symlexvpn.com/wp-content/uploads/2026/01/Ultimate-White-Label-VPN-Business-Guide-2025-Cost-ROI_2-376x114.webp)