
Discover How VPN Tunneling Is Accomplished: Unveil the Secret!
- August 29, 2023
- 8 minutes Read
- VPN Service
Have you ever wondered how VPN tunneling works and how it keeps your online activities secure? Let’s unveil the secret behind how VPN tunneling is accomplished.
VPN tunneling encrypts data as it travels from your device to the VPN server. It acts as a protective shield, preventing anyone from intercepting or accessing your data. It protects you from cyberattacks like Man-in-the-middle attack (MITMA), eavesdropping, and potential data leaks.
Do you want to know more about VPN tunneling? Read on to learn more about this tunneling technology and how it can help safeguard your online privacy and security.
Table of contents
How Does a VPN Tunnel Work?
Source: https://www.youtube.com/
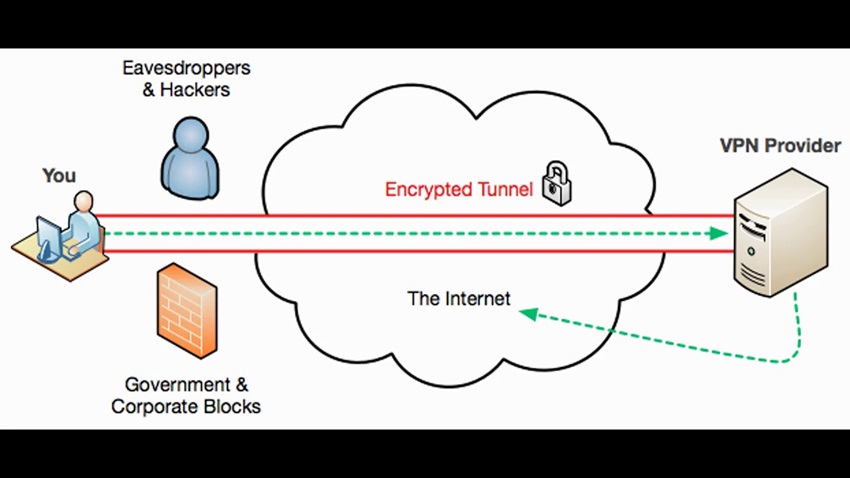
VPN tunnels protect your online activity by establishing an encrypted connection between your device and a VPN server. Here’s a brief explanation of how a VPN tunnel works and secures the incoming and outgoing connections.
- Establishing a VPN connection: Once you connect to a VPN, your device establishes a secure connection with the VPN server. This connection is encrypted to ensure the privacy and security of your data.
- Data encapsulation: Once the connection is established, your data is split into smaller packets and encapsulated within other data packets. This process is known as encapsulation or tunneling.
- Encrypting the data: The encapsulated data is then encrypted, making it unreadable to anyone intercepting it. Encryption ensures that your data remains secure and protected from unauthorized access.
- Routing through the tunnel: The encrypted data packets are then sent through the VPN tunnel to the VPN server. The VPN server acts as an intermediary between your device and the internet.
- Leaving the tunnel: Once the data reaches the VPN server, it is decrypted and sent out to its intended destination on the internet. Throughout this process, your data is kept private and secure from unauthorized access.
Now that we know how VPN tunneling is accomplished, let’s take a look at the different tunneling protocols and their functionalities.
Which Types Of VPN Tunneling Are There?
There are a wide variety of VPN tunneling protocols. Let’s find out the details.
WireGuard
Wireguard protocol offers fast speed, robust security, compatibility, and ease of use. It’s a suitable protocol for quick downloads, non-lag gaming, and streaming. Moreover, it has only 4000 lines of code, making it the lightest protocol.
Speed: Fastest speed
Security: Best security
IPSec/IKEv2
IPSec/IKEv2 is a VPN protocol that establishes secure VPN communication between VPN devices. This protocol is ideal for gaming, streaming, and smooth internet browsing. However, it only offers UDP protocol.
Speed: Quite fast
Security: High security
OpenVPN
OpenVPN is an open-source VPN protocol that is regarded as one of the most secure and reliable. Its strong encryption capabilities, ease of use, and compatibility make it the best choice for both individuals and companies.
Speed: Very fast
Security: High security
SSTP
SSTP (Secure Socket Tunneling Protocol) is a VPN protocol that was developed by Microsoft. Its robust security features and ability to circumvent firewalls make it a popular choice for Windows users.
Speed: Medium speed
Security: High security
L2TP/IPSec
Layer 2 Tunneling Protocol (L2TP) provides a good amount of security and privacy. It provides good security and ease of use. However, it can be blocked by firewalls due to using the UDP 500 protocol.
Speed: Medium speed
Security: Medium security
PPTP
PPTP (Point-to-point tunneling protocol) is one of the oldest VPN protocols that doesn’t require any additional software to install. It’s a good choice for those who want to enjoy smooth gaming and streaming experience. However, it’s not ideal for security due to having a lot of security vulnerabilities.
Speed: Quite fast
Security: Poor security
What is Split Tunneling In VPNs?
The split tunneling feature of a VPN allows you to route some of your internet traffic through an encrypted VPN tunnel while routing the rest through an open tunnel.
Split tunneling allows you to choose which applications can use the VPN network and which are not.
It is particularly useful when you want to access both secure resources simultaneously, such as company resources through a VPN and personal internet resources. By splitting traffic, businesses can conserve bandwidth, improve internet speeds, and keep business resources secure while allowing employees to access personal resources.
Through split tunneling, employees can access both their local area network and other networks without disconnecting and reconnecting to their VPN connections.
What Is GRE Tunneling In VPNs?
The GRE (Generic Routing Encapsulation) tunneling protocol is used in VPNs to encapsulate a variety of network protocols within virtual point-to-point links. The protocol creates a secure channel for sending data between networks.
GRE tunnels provide a private and secure path for transporting packets through a public network by encapsulating the packets. This allows for the transmission of different network layer protocols, such as IPX and AppleTalk, over an IP network.
GRE tunneling is commonly used in WAN 2.0 technology to connect private networks across shared or public network infrastructure. The protocol provides a reliable, efficient method for establishing secure communication over networks.
What Is SSH Tunneling in VPNs?
SSH (Secure Shell) tunneling is a technique used in VPNs to create a secure connection between two points in a network. SSH encapsulates network traffic within an SSH connection while encrypting and authenticating the data.
By using SSH tunnelling, users can bypass firewalls and other network restrictions by sending traffic through an encrypted tunnel that cannot be detected.
It is also used to secure remote access to network resources, such as servers and databases. SSH tunneling can be used in combination with other VPN protocols, such as OpenVPN and IPSec, to provide an additional layer of security.
Overall, SSH tunneling is a powerful tool for securing network traffic and providing secure remote access to network resources.
How Can You Test a VPN Tunnel?
You can test whether your VPN tunneling is working properly or not. There are three methods: IP leak test, DNS leak test, and WebRTC leak test.
- IP leak test: You can use various online tools to check your IP address—for example, whatismyipaddress, whatismyip, lookup, etc. After connecting to a VPN server, go to one of these websites to check your IP address. If it still shows your original IP, then your IP is leaking potentially exposing your online identity.
- DNS leak test: Go to the DNS Leak Test website and hit “Standard test”/” Extended test”. The website will perform a DNS leak test and show you a list of your VPN servers. If the IP address matches the VPN server you’re connected to, there is no DNS leak. However, if you see your real IP address on the list, it means there’s a potential DNS leak.
- WebRTC leak test: Head to the Browser Leaks website, and it automatically shows you if there’s a WebRTC leak. To prevent WebRTC leaks, you can disable WebRTC in your browser or use a VPN that offers WebRTC leak protection.
FAQs
Can tunneling affect VPN performance?
Yes, tunneling can affect VPN performance to some extent. The choice of tunneling protocol can impact factors like connection speed and overall performance. PPTP, for example, offers faster speeds but with less security. In contrast, OpenVPN has strong safety, but it might slow down connection speeds.
What is the difference between a VPN and a VPN tunnel?
VPN provides a secure connection between you and the internet, whereas VPN tunnels encrypt connections between devices and VPN servers. A wide range of VPN tunnels are used for different purposes. Some tunnels are better for security, while some tunnels provide good speed for gaming and streaming.
What is the best tunneling protocol?
Wireguard and OpenVPN is, overall the best tunneling protocol in terms of security, speed, and reliability. Wireguard offers the best speed while maintaining strong security. But it only gives UDP for faster connections. While OpenVPN provides the best security, it is slower due to its strong encryption, which can be annoying.
Final Words
VPNs are essential in 2024 if you want to protect yourself in public Wi-Fi networks, prevent cyber attacks, and bypass geo-blocks and censorships. They allow you to surf the web anonymously, securely, and privately while also providing access to restricted content and services. Therefore, it’s important to choose the right VPN to make sure your data remains secure, and your online activities remain private. One of the significant benefits of VPN tunneling is its ability to prevent Google from tracking your online activities. By encrypting your internet traffic and masking your IP address, a VPN ensures that your browsing history remains private and secure.
![Ultimate White Label VPN Business Guide 2026 [Cost & ROI]](https://symlexvpn.com/wp-content/uploads/2026/01/Ultimate-White-Label-VPN-Business-Guide-2025-Cost-ROI_2-376x114.webp)




