AES-256 vs AES-128: Head to Head
- May 29, 2024
- 8 minutes Read
- Security & Privacy
We all have at least once heard about AES encryption, but do you know who is behind this brilliant cryptography? Its original name is Rijndael encryption, developed by two Belgian cryptographers, Vincent Rijmen and Joan Daemen.
It is now widely used as an AES encryption algorithm on many platforms by the US federal government, militaries, law enforcement agencies, Virtual Private Networks, and cybersecurity services for its unbreakable security and strength.
In general, AES-256 is stronger, faster, and more secure than AES-128-bit encryption. However, you won’t feel any difference as a general user.
The AES 128-bit is strong enough for fundamental security needs. The AES-256 algorithm is designed for enterprise-level security.
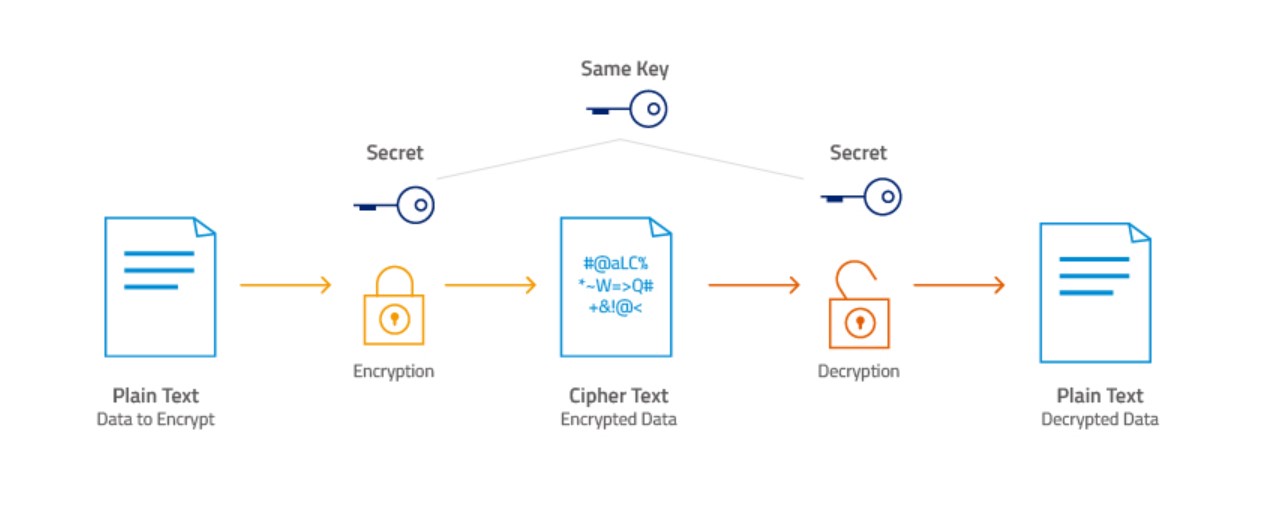
Table of contents
What is the Advanced Encryption Standard (AES)?
The Advanced Encryption Standard (AES) is a widely used symmetric-key encryption algorithm used to protect sensitive data.
It was established by the U.S. National Institute of Standards and Technology (NIST) in 2001, after a lengthy standardization process and public competition.
Since then, AES has become the de facto standard for encryption and is used in various applications and protocols.
Brief Comparison At a Glance
Here’s a brief comparison table on AES-256 vs AES-128 bit encryption.
| Feature | AES-256 | AES-128 |
| Key Size | 256 bits | 128 bits |
| Security Level | Higher security level due to larger key size | Considered secure for most applications |
| Brute-Force Resistance | Stronger resistance against brute-force attacks | Lower resistance compared to AES-256 |
| Performance | Slightly slower than AES-128 due to the larger key size | Faster than AES-256 |
| Energy Consumption | Higher energy consumption (relevant for mobile devices) | Lower energy consumption |
| Hardware Support | Widely supported in modern hardware | Widely supported in modern hardware |
| Use Cases | Recommended for high-security applications (e.g., government, military, financial) | Suitable for most commercial applications |
| Compatibility | Compatible with older systems and applications | Compatible with older systems and applications |
AES-256: The Stronger Sibling
Key Size
As the name suggests, the AES-256 bit has a key size of 256 bits. It provides a higher level of security due to an insignificantly large number of keys.
A larger length of key size means it’s harder to crack. AES 256-bit encryption has 2^256 keys, making it much harder for hackers to perform brute-force attacks.
Even quantum computers with ridiculously high processing power would take around 3.31 x 1056 years to crack an AES-256-bit encryption (it’s not going to happen anyway).
Security Level
AES-256-bit encryption is considered the strongest encryption algorithm that exists. That’s why it’s also called military-grade encryption. AES 256 is used by the US federal government, militaries, banks, and other organizations like law enforcement.
Brute-Force Resistance
AES-256 is extremely strong against brute-force attacks. Because of its large key size would take supercomputers trillions of years to crack and decipher AES-256 keys. That’s why the US government and militaries use AES for secure communications.
Performance
AES-256 bit is comparatively slower due to its large key size. The encryption in AES 256 involves multiple rounds of data substitution, permutations, and mixing.
This complex encryption process slightly affects the performance at the cost of strong security. Due to its large key length, it becomes challenging for the attackers to crack and decipher the data, ensuring long-term security in the era of quantum computing.
Energy Consumption
AES 256-bit has a higher energy consumption due to its heavy encryption, which needs more computational power. Different modes of AES operation, such as ECB, CBC, CFB, and CTR, impact energy consumption differently.
Additionally, performance depends on the hardware and software implementation, as well as the key size of the encryption standard. The average energy consumption for decryption was noted to be approximately 30% more than for other encryptions.
Hardware Support
AES 256 encryption is widely used and supported by all major hardware and software. It’s supported by various CPU architectures such as x64, x86, and ARMv8.
The .NET framework supports hardware AES acceleration through the AesCryptoServiceProvider class. Routers with ARMv8 processors support AES encryption, which offers improved performance.
Use Cases
In 2024, it will be mostly used for secure communication, banks, credit card issuers, file sharing, cloud security, and cybersecurity, such as Virtual Private Networks (VPN). Nowadays VPN adoption rate is increasing day by for for online security which is why providers tend to use the best protection available out ther for robust data security.
Compatibility
AEs 256-bit is compatible with older hardware and applications. That reduces the chances of incompatibility issues in outdated hardware and software on all platforms.
Download iPhone VPN App
Download Android VPN App
AES-128: The Efficient Alternative
Key Size
AES-128 consists of a 128-bit key that is comparatively shorter than AES-256. Despite the key size, AES-128 is a robust encryption algorithm that provides unbreakable security. With the key size, it would take around 1.02 x 1018 years for even supercomputers to crack and decipher the encryption.
Security Level
AES-128 offers the same security and protection as AES-256 bit. As a general user, you won’t feel any difference; honestly, you don’t need more than 128 bits of AES protection. AES-128 is enough for applications’ day-to-day security standards.
Brute-Force Resistance
AES-128 is also super strong against brute force attacks. Even with quantum technologies, cracking an AES-128-bit encryption would take one billion years.

Performance
AES-128 bit involves a lesser encryption process than AES-256, which is why it performs slightly better—the more complex the encryption, the more computational power it requires, impacting overall performance. Since AES-128-bit encryption has a shorter key size, it’s less complicated than AES-256.
Energy Consumption
AES-128 consumes less energy than AES-256-bit encryption since it requires less resources and CPU power. It’s ideal for handy devices that need more standby power.
Hardware Support
AES-128 encryption provides excellent hardware support similar to other AES ecnyptions. Many modern CPUs from Intel, AMD include dedicated instruction set extensions for accelerating AES operations–AES-NI (Intel Advanced Encryption Standard New Instructions) and AMD’s AES instructions.
Use Cases
AES-128 is commonly used for encrypting files, folders, and entire disk volumes on various operating systems, including Windows (BitLocker), macOS (FileVault), and Linux (LUKS, eCryptfs). It provides confidentiality for sensitive data at rest, such as documents, databases, and backups.
Compatibility
AES-128 is a widely adopted and standardized encryption algorithm, ensuring compatibility across different platforms, operating systems, and applications.
Its widespread use and support by various software and hardware vendors make it a reliable choice for secure data exchange between different systems.
Source: https://www.logsign.com/
Choosing the Right AES Variant
When deciding between AES-256 and AES-128, there are several factors to consider:
Security Requirements
- AES-256 offers a higher level of security compared to AES-128 because of its longer key length (256 bits vs. 128 bits). The longer the key length, the more resistant the algorithm is to brute-force attacks.
- AES-256 is recommended for applications that require a higher level of confidentiality, such as military, government, or highly sensitive commercial applications.
- If the encrypted data is extremely valuable or sensitive, and long-term protection is crucial, AES-256 may be the preferred option.
Performance Requirements
- AES-128 is generally faster than AES-256 in terms of encryption and decryption speeds, especially on hardware without dedicated AES acceleration.
- For applications with high-throughput requirements or real-time constraints, AES-128 may be preferred to minimize computational overhead.
- If performance is a critical factor, and the data does not require the highest level of security, AES-128 can be a suitable choice.
Hardware and Software Constraints
- Some hardware or software platforms may have limited support or optimizations for AES-256, making AES-128 a more compatible choice.
- Older or resource-constrained devices, such as embedded systems or legacy applications, may not have efficient implementations of AES-256, leading to performance degradation.
Battery Life Considerations (for mobile devices)
- On mobile devices or Internet of Things (IoT) devices with limited battery power, the increased computational overhead of AES-256 may result in faster battery drain compared to AES-128.
- If battery life is a critical factor, and the security requirements are not extremely high, AES-128 may be a more suitable choice.
Wrapping Up
In the battle of AES 256 vs AEs 128 the ultimate choice depends on user preferences. Both are state-of-the-art encryption standard for protecting modern technologies. Hope the information provided in this write-up will help you decide which one is right for you.
Symlex VPN uses cutting edge AES-256 bit encryption method for maximum security. Try Symlex VPN premium free backed by 7-days money back guarantee.
![Ultimate White Label VPN Business Guide 2026 [Cost & ROI]](https://symlexvpn.com/wp-content/uploads/2026/01/Ultimate-White-Label-VPN-Business-Guide-2025-Cost-ROI_2-376x114.webp)