DoS vs. DDoS Attacks: What’s the Difference?
- July 18, 2024
- 11 minutes Read
- Security & Privacy
DoS and DDoS attacks are notorious cyberattacks that disrupt a network or a system.
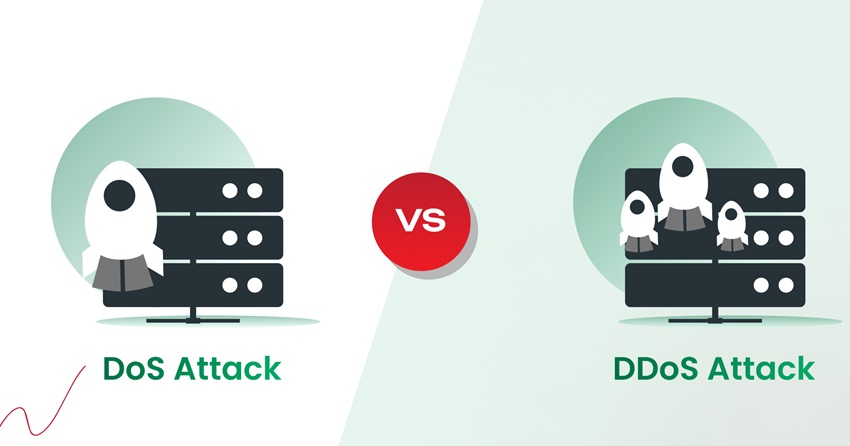
A DoS attack involves a single device overwhelming a target with excessive traffic.
Alternatively, a DDoS attack uses multiple devices controlled by a botnet to flood the target with traffic, making it more difficult to defend.
While both types of attacks aim to disrupt the availability of online resources, the process and implications can vary significantly.
There are three common types of DDoS attacks:
- Volumetric Attack
- Protocol DDoS attacks
- Application DDoS attacks
Understanding the nuances of DoS and DDoS attacks is crucial for developing effective defense strategies and safeguarding against DDoS attacks. This article will explore these attacks’ key differences, characteristics, and prevention methods.
Table of contents
- What is Denial of Service (DoS)?
- What is Distributed Denial of Service (DDoS)?
- DoS vs. DDoS: Quick Comparison
- 7 Types of DoS and DDoS Attacks Explained
- How to Prevent DoS and DDoS Attacks?
- How VPNs Protect Against DoS and DDoS Attacks?
- Famous DDoS Attacks that Took Place
- Frequently Asked Questions (FAQs)
- Final Thoughts
What is Denial of Service (DoS)?
A DoS attack involves a single device or source overwhelming a target system or network with excessive traffic, requests, or malicious actions.
This overload of resources can cause the target to become unavailable, denying legitimate users access to the affected services.
DoS attacks often exploit vulnerabilities in the target’s infrastructure or software, leveraging techniques such as SYN floods, UDP floods, or application-layer attacks to exhaust the system’s resources.
DoS attacks are often conducted with LOIC/HOIC programs through botnets.
What is Distributed Denial of Service (DDoS)?
A Distributed Denial-of-Service (DDoS) attack is a more sophisticated DoS attack that uses multiple sources to launch the attack from various locations simultaneously.
This makes DDoS attacks more difficult to mitigate than traditional DoS attacks. The critical difference is that a DoS attack originates from a single source.
Alternatively, a DDoS attack comes from multiple distributed sources, making identifying and blocking the attack harder.
DoS and DDoS attacks can significantly impact organizations, causing disruptions, financial losses, and reputational damage.
Defending against these attacks requires a combination of technical measures, incident response planning, and ongoing monitoring and mitigation efforts.
DoS vs. DDoS: Quick Comparison
| Factor | Denial of Service (DoS) | Distributed Denial of Service (DDoS) |
| Attack Origin | Single source | Multiple distributed sources |
| Attack Scale | Limited | Large-scale |
| Attack Mechanism | Overwhelming a target system with traffic from a single source | Overwhelming a target system with traffic from multiple distributed sources |
| Difficulty to Execute | Relatively easier | More complex to orchestrate |
| Impact | Can disrupt service temporarily | Can cause prolonged service disruption |
| Detectability | Easier to detect and mitigate | More challenging to detect and mitigate |
| Motivation | Personal, political, or ideological reasons | Often financially motivated or used as a distraction for other malicious activities |
| Examples | Flooding a website with HTTP requests, exhausting system resources | Botnet-powered attacks targeting a server or network with massive traffic |
7 Types of DoS and DDoS Attacks Explained
Seven major types of DoS and DDoS attacks include ping of death, SYN flood, UDP flood, HTTP flood, zero-day attack, etc.
These attacks are usually conducted through programs like Low Orbit ION Cannon (LOIC) and High Orbit Cannon (HOIC), which use botnets or ghost PCs.
Low Orbit Cannon (LOIC)
LOIC is a simple DoS/DDoS attack tool that overwhelms a target with traffic from a single device. It allows users to specify the target’s IP address and port and the type of attack to launch. LOIC is often used in coordinated attacks, with multiple users targeting the same victim simultaneously.
However, its simplicity and reliance on a single source make it less effective against sophisticated DDoS defenses than more advanced DDoS tools.
High Orbit Cannon (HOIC)
HOIC is a more advanced DDoS tool that can generate a higher traffic volume from multiple sources, making it more effective against DDoS mitigation measures.
Unlike LOIC, HOIC utilizes a distributed network of devices, often controlled by a botnet, to overwhelm the target with a coordinated attack. This distributed nature makes HOIC-based DDoS attacks more challenging to detect and mitigate, as the traffic originates from various locations simultaneously.
Defending against HOC-powered DDoS attacks requires robust network monitoring, traffic analysis, and advanced DDoS mitigation strategies.
Let’s discuss the seven major types of DoS/DDoS attacks.
Ping of Death
The Ping of Death (PoD) is a denial-of-service (DoS) attack in which malformed or oversized ping packets are sent to a target system to crash or destabilize it.
An oversized packet attack exploits a vulnerability in the TCP/IP protocol stack, causing the target system to crash or reboot as a result.
Defending against Ping of Death attacks involves implementing proper packet size validation and network monitoring to detect and block malformed ICMP packets.
SYN Flood
A SYN flood attack overwhelms a target’s resources by sending many TCP connection requests (SYN packets) without completing the three-way handshake.
This can exhaust the target’s connection queue, making it unable to respond to legitimate connection requests. Mitigation strategies include SYN cookies, connection limit enforcement, and using load balance.
UDP Flood
UDP Flood attack is a type of volumetric DDoS attack that exploits the connectionless nature of the User Diagram Protocol (UDP). Unlike the Transmission Control Protocol (TCP). UDP does not require a handshake to establish a connection.
Attackers can leverage this by sending a large number of UDP packets to random ports on the target system, exhausting its resources, and denying service to legitimate users.
Mitigating UDP flood attacks involves implementing techniques such as rate limiting, blacklisting, and using advanced DDoS protection services.
HTTP Flood
An HTTP flood is a type of DDoS attack that targets web servers by sending many legitimate-looking HTTP requests, overwhelming the server’s resources and disrupting normal operation. This attack aims to exhaust the target’s CPU, memory, or network bandwidth, making the website or web application unavailable to legitimate users.
Defending against HTTP floods requires techniques like rate limiting, CAPTCHA challenges, and leveraging content delivery networks (CDNs) or cloud-based DDoS mitigation services.
Zero-day Attack
A zero-day attack is a comparatively newly discovered security attack that hackers can use to bring down systems.
This attack occurs when hackers exploit a previously unknown vulnerability in software or systems for which no patch or security fix is available.
This attack takes advantage of a vulnerability in the HTTP/2 protocol to launch massive, hyper-volumetric Distributed Denial of Service (DDoS) attacks.
Buffer Overflow
To better understand buffer overflow, we must first understand a buffer. A buffer is a storage device in physical memory that temporarily stores data while being transformed from one place to another.
A buffer overflow attack occurs when a program attempts to store more data in a buffer than it can accommodate, causing the system to malfunction.
This type of attack aims to overwrite the program’s memory, potentially allowing the attacker to execute arbitrary code on the target system.
Defending against buffer overflow attacks requires secure coding practices, such as input validation, bounds checking, and memory-safe programming languages.
To mitigate these issues, systems need runtime protection like Address Space Randomization, and Data Execution Prevention (DEP) methods can be taken.
DNS Amplification Attack
A DNS amplification attack is a type of DDoS attack that exploits vulnerabilities in the Domain Name System (DNS) protocol. Attackers send several spoofed DNS requests to open DNS resolvers, which then respond with much larger DNS response packets, amplifying the traffic and overwhelming the target system.
Mitigating DNS amplification attacks requires implementing DNS best practices, such as rate limiting, blocking spoofed traffic, and using DNS firewalls or cloud-based DDoS protection services. Ongoing monitoring and updating of DNS infrastructure are also crucial to stay ahead of evolving attack techniques.
How to Prevent DoS and DDoS Attacks?
There are multiple ways to prevent DoS and DDoS attacks.
Implement DDoS Protection Services
Deploy DDoS protection services to safeguard against attacks that overwhelm your network with excessive traffic. These services filter and block malicious traffic, ensuring continuous availability and protecting against service outages.
Modern solutions use advanced algorithms and machine learning for real-time threat detection and mitigation. Implementing DDoS protection enhances security, maintains customer trust, and ensures reliable operations.
Ensure Adequate Network Capacity
Ensuring adequate network capacity prevents performance bottlenecks and service disruptions during peak usage. Regularly assess your network’s load and forecast future demands. Upgrade infrastructure and utilize scalable cloud services and CDNs to handle increased traffic. Proactively managing network capacity ensures a seamless user experience and reliable service.
Implement Access Controls
Implement access controls to protect sensitive data from unauthorized access. Use multi-factor authentication (MFA), role-based access control (RBAC), and the principle of least privilege (PoLP). MFA adds extra security layers, RBAC assigns permissions based on roles, and PoLP minimizes access privileges. Regularly update access controls to adapt to changing security needs.
Keep Software Up-to-Date
Update software regularly to patch vulnerabilities and protect against cyber threats. Updates include security enhancements and bug fixes for operating systems, applications, firmware, and plugins.
Maintain a software asset inventory and automate the software update process. Software updates ensure your IT infrastructure’s security, stability, and performance.
Monitor and Analyze Network Traffic
Continuously monitor and analyze network traffic to detect and respond to suspicious activities. Use tools like intrusion detection systems (IDS) and intrusion prevention systems (IPS) for real-time monitoring and alerts.
Analyzing traffic helps identify patterns and anomalies, optimize network performance, and enhance security. Proactive monitoring ensures reliable network operations.
Have an Incident Response Plan
Develop an incident response plan to manage and mitigate security breaches. The plan should include preparation, identification, containment, eradication, recovery, and lessons learned.
Establish an incident response team, define roles, and regularly test and update the plan. Effective incident response minimizes damage, ensures quick recovery, and improves future security measures.
How VPNs Protect Against DoS and DDoS Attacks?
For Individuals
A VPN (Virtual Private Network) can prevent DoS (Denial of Service) and DDoS (Distributed Denial of Service) attacks by hiding your IP address. Attackers find it hard to locate and target your network when your IP is hidden. VPNs encrypt your internet traffic, making it difficult for attackers to intercept your data.
When you use a VPN, your online activities are more private. Your ISP and other intermediaries cannot see your browsing habits. This encryption adds an extra layer of security, making it challenging for attackers to launch DoS or DDoS attacks.
A VPN protects personal data and prevents disruptions to individuals’ online activities. It keeps your internet connection safe and private. This protection is crucial for gaming, streaming, and online banking, where interruptions can be particularly frustrating.
For Businesses
A VPN secures the company’s network, protecting sensitive information from unauthorized access. By hiding the IP addresses of business servers, VPNs make it difficult for attackers to find and target them.
A VPN helps prevent service outages caused by DoS and DDoS attacks, ensuring smooth operation. Businesses that rely on constant online presence can avoid costly downtime. The encryption provided by VPNs ensures that confidential business communications and data transfers are secure.
Using a VPN is a key step in a comprehensive security strategy. It reduces the risk of cyberattacks, safeguards critical data, and maintains the trust of clients and stakeholders. For both individuals and businesses, a VPN provides an essential layer of defense against DoS and DDoS attacks.
Famous DDoS Attacks that Took Place
Some famous DDoS attacks include the 2016 Dyn attack, which disrupted major websites, and the 2018 GitHub attack, one of the largest DDoS attacks on record.
These attacks highlight the need for robust DDoS mitigation strategies to ensure business continuity and protect against the crippling effects of such cyber threats.
To protect against DDoS attacks, it is important to stay vigilant, implement security best practices, and collaborate with cybersecurity experts.
Frequently Asked Questions (FAQs)
What are common indications of a DoS or DDoS attack?
Some common indications of a DoS attack include low network performance, difficulty accessing websites, website unavailability, and Inability to access a web service. Also, an increase in spam emails may be used to send emails. Unusual traffic spikes in requests from multiple locations or IP addresses indicate DoS to DDoS attack.
What is a real-life example of DoS?
A prominent real-life example of a Denial of Service (DoS) attack is the “Mirai” botnet attack, which took place in October 2016. This attack targeted Internet of Things (IoT) devices, including IP cameras, routers, and digital video recorders (DVRs).
What is a Layer 7 attack?
An Application-Layer DDoS attack, also known as a Layer 7 (L7) attack, targets the top layer of the OSI model. It specifically targets disrupting services like HTTP GET and POST requests by overwhelming them with malicious traffic. This type of attack focuses on the web application level, making it difficult to detect and mitigate.
Final Thoughts
The increasing frequency of denial-of-service (DoS) and Distributed denial-of-service (DDoS) attacks highlights the need for strong cybersecurity strategies to protect businesses and their digital assets.
In order to prevent these damaging online attacks, businesses should adopt DDoS defense solutions, implement access restrictions, update applications regularly, monitor network data flow, and develop a clear plan to handle cyber incidents.