
Perfect Forward Secrecy for VPNs: Ultimate Protection Against Future Data Breaches
- 11 月 5, 2025
- 17 分钟阅读
- 虚拟专用网
Perfect forward secrecy in reliable VPNs generates unique encryption keys for each VPN session that disappear permanently after disconnection, protecting your browsing history even if hackers steal server keys years later.
目录
- TL;DR – Key Takeaways
- What Perfect Forward Secrecy Means for VPN Security
- How Perfect Forward Secrecy Protects Your VPN Sessions
- Real-World Benefits That Matter for VPN Users
- VPN Protocols Supporting Perfect Forward Secrecy
- Verifying Perfect Forward Secrecy in Your VPN Service
- Leading VPN Providers with Verified Perfect Forward Secrecy
- Perfect Forward Secrecy Integration with Other Security Features
- Common Implementation Problems and Red Flags
- Future Evolution of Perfect Forward Secrecy Technology
- Selecting VPNs with Reliable Perfect Forward Secrecy
- Performance Considerations and Real-World Impact
- Common Misconceptions and Security Limitations
- Choosing the Right Perfect Forward Secrecy VPN
- 包起来
- 常见问题解答
TL;DR – Key Takeaways
Perfect forward secrecy transforms VPN security by creating temporary session keys that vanish after each connection. This prevents hackers from decrypting your past internet activities, even if they compromise your VPN provider’s servers in the future.
为什么它很重要:
- Protects against “harvest now, decrypt later” surveillance
- Contains breach damage to current sessions only
- Shields historical data from quantum computing threats
- Essential for journalists, activists, and privacy-conscious users
Top providers: ExpressVPN, ProtonVPN, NordVPN, and Mullvad all implement verified perfect forward secrecy with automatic key rotation.
What Perfect Forward Secrecy Means for VPN Security
完美前向保密(PFS) creates temporary keys for each VPN session that prevent hackers from decrypting your past browsing data, even if they steal your provider’s main encryption keys later.
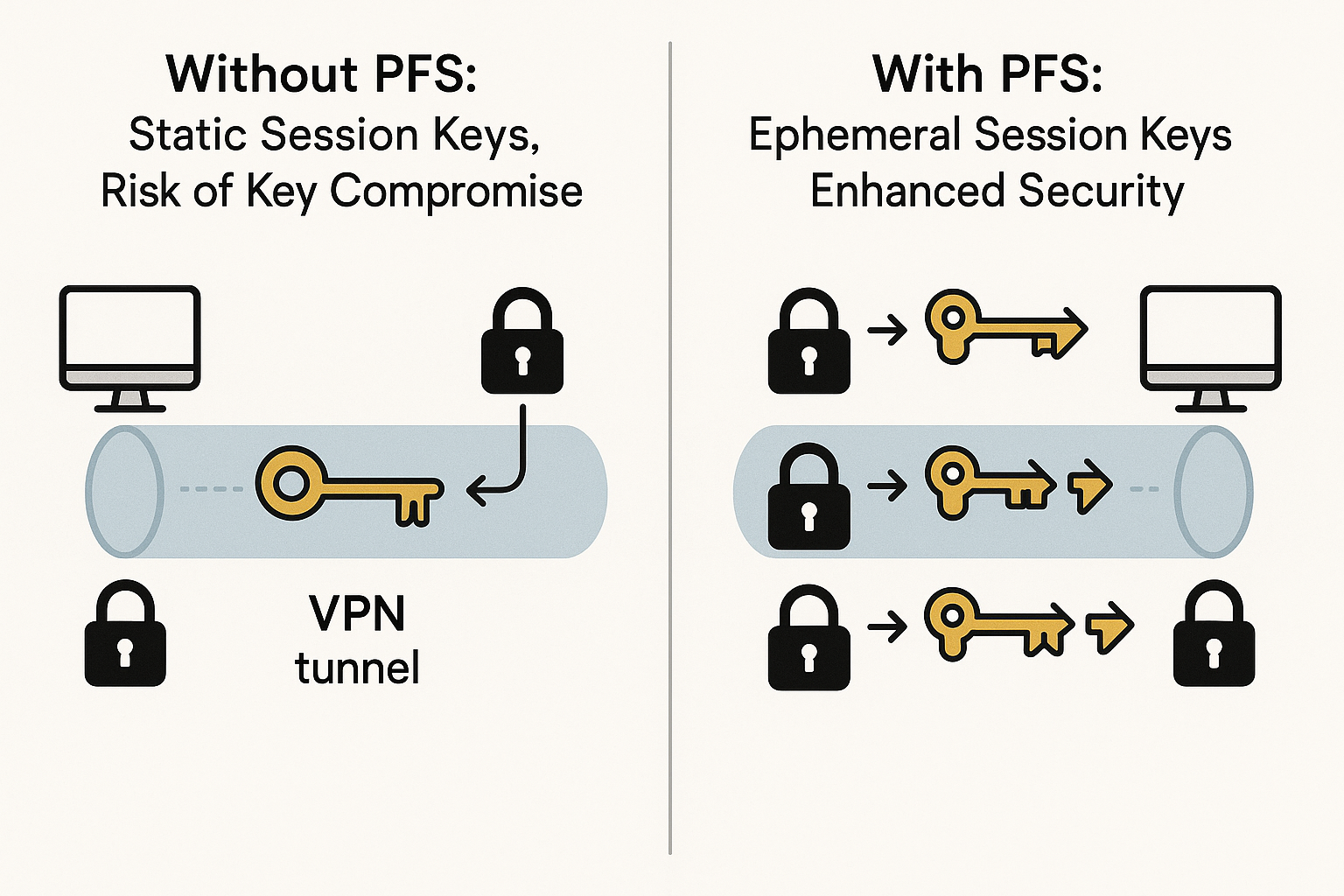
Perfect forward secrecy ensures that compromising long-term encryption keys cannot decrypt past communications by using ephemeral session keys that exist only during individual connections.
Unlike traditional encryption that reuses master keys across multiple sessions, perfect forward secrecy treats each VPN connection as a completely isolated security event.
The technical foundation operates through ephemeral key exchange algorithms, primarily Diffie-Hellman (DHE) or Elliptic Curve Diffie-Hellman (ECDHE) protocols.
These mathematical processes enable your device and VPN server to generate identical encryption keys without transmitting sensitive key material across the internet.
Traditional VPN encryption resembles having the same house key for years. If someone eventually steals that master key, they gain access to everything you’ve ever done behind that door. Perfect forward secrecy changes the locks automatically every time you enter, rendering stolen keys useless for accessing past activities.
When you initiate a secure VPN connection, both systems generate random mathematical values that combine through cryptographic algorithms to produce matching session keys. These keys encrypt your internet traffic throughout that specific session and face immediate destruction upon disconnection.
How Perfect Forward Secrecy Protects Your VPN Sessions
Perfect forward secrecy begins working during your VPN’s initial handshake sequence when your device contacts the server. Both parties first authenticate using permanent certificates to verify legitimate connection attempts and prevent impersonation attacks.
The temporary key generation phase utilizes sophisticated mathematical protocols where both your device and the VPN server create random numbers that never leave their respective systems. Through cryptographic calculations, they derive identical session keys without exposing sensitive information to potential network eavesdroppers.
Your internet traffic receives encryption using these unique session keys throughout the VPN session. Browsing activities, streaming content, file transfers, and communications remain completely private using encryption keys that exist nowhere else in the digital world.
Key destruction occurs immediately when your VPN session terminates through disconnection, network changes, or timeout periods. Both systems permanently delete these temporary keys through irreversible processes that prevent recovery even with advanced forensic techniques.
Advanced VPN security implementations automatically refresh encryption keys during extended sessions. Leading providers rotate keys every 15 minutes to several hours, providing continuous protection against sophisticated prolonged attacks targeting active connections.
Real-World Benefits That Matter for VPN Users
Defeating Mass Surveillance Programs
Intelligence agencies and criminal organizations deploy “harvest now, decrypt later” strategies where they collect encrypted traffic hoping to decrypt it later. Perfect forward secrecy makes these surveillance programs ineffective by ensuring past sessions remain unreadable even when master keys get compromised.
Key protection benefits include:
- Archives encrypted traffic becomes permanently unreadable
- Government surveillance programs cannot retroactively access browsing history
- Legal pressure on VPN providers cannot expose past user activities
- Mass data collection efforts yield no historical information
Containing Security Breach Damage
When VPN providers face security incidents, perfect forward secrecy limits damage to current active sessions rather than exposing comprehensive user histories. This containment creates economic disincentives for targeting secure VPN infrastructure.
Breach limitation advantages:
- Attackers access only minimal current session data
- Years of user browsing history remain protected
- Reduced motivation for sophisticated attacks on secure providers
- Limited information value decreases targeting likelihood
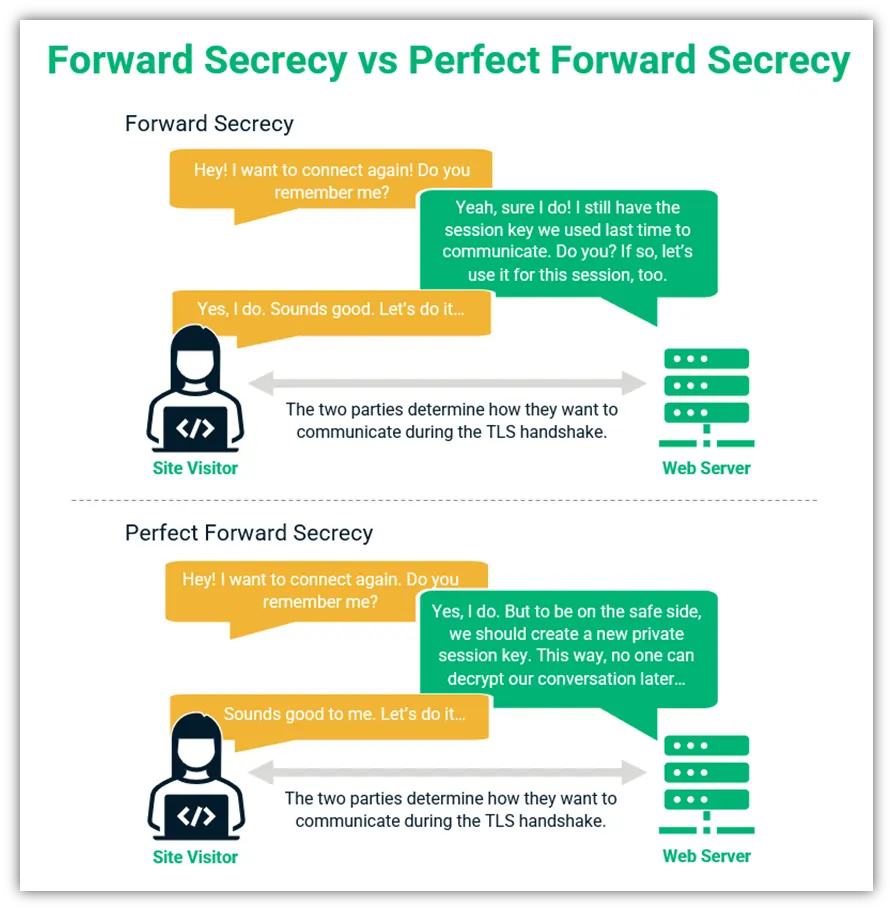
Image source: Sectigo Store
Protecting Against Quantum Computing Threats
Quantum computers threaten current encryption algorithms but perfect forward secrecy provides protection by ensuring today’s traffic remains secure against tomorrow’s computing advances.
Quantum resistance features:
- Session keys destroyed before quantum computers can break them
- Historical communications remain secure despite future algorithm breaks
- Long-term privacy protection against technological advances
- Future-proofed security for sensitive activities
Enhanced Security for High-Risk Users
Journalists, activists, and business professionals face elevated surveillance risks requiring additional protection beyond standard privacy measures.
Perfect forward secrecy enables confident VPN usage in high-risk scenarios.
High-risk user benefits:
- Source communications remain protected indefinitely
- Sensitive research activities stay secure long-term
- Authoritarian government surveillance cannot access historical data
- Professional confidentiality maintained against future threats
VPN Protocols Supporting Perfect Forward Secrecy
OpenVPN with ECDHE Configuration
OpenVPN supports perfect forward secrecy when configured with Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) key exchanges.
Implementation quality varies significantly between providers.
Configuration characteristics:
- Premium providers enable ECDHE by default with AES-256 encryption
- Budget services may skip implementation to reduce server costs
- Proper configuration requires 4096-bit keys for maximum security The encryption strength becomes critical with OpenVPN implementations requiring proper ECDHE configuration for genuine perfect forward secrecy protection.
WireGuard Protocol Advantages
WireGuard incorporates perfect forward secrecy as a fundamental design principle with automatic key rotation every few minutes during active sessions.
WireGuard benefits:
- Built-in perfect forward secrecy requires no additional configuration
- Automatic key refresh during network transitions
- Streamlined codebase enables easier security auditing
- Optimal for mobile devices switching between networks
- Superior performance compared to traditional protocols
IKEv2/IPSec Implementation Considerations
Internet Key Exchange version 2 supports perfect forward secrecy through ephemeral Diffie-Hellman exchanges when properly configured on both client and server systems.
IKEv2 implementation factors:
- Requires careful configuration matching between systems
- Default to basic key exchange without ephemeral properties
- Protocol complexity can lead to configuration mismatches
- Mobile network transitions handled effectively when configured properly
- Provider transparency about configuration details remains essential
Modern Proprietary Protocols
Leading VPN companies have developed custom protocols incorporating perfect forward secrecy optimization. ExpressVPN’s Lightway protocol and NordVPN’s NordLynx (based on WireGuard) both implement automatic key rotation with performance optimizations unavailable in generic implementations.
These proprietary solutions often provide superior performance characteristics while maintaining security transparency through open-source components and independent security audits validating their perfect forward secrecy implementations.
Verifying Perfect Forward Secrecy in Your VPN Service
Documentation and Transparency Analysis
Reputable VPN providers explicitly detail perfect forward secrecy support in technical specifications and security documentation. Genuine implementation requires specific technical details rather than vague marketing language.
Documentation verification checklist:
- Look for specific mentions of ECDHE or ephemeral key exchanges
- Check for automatic key rotation frequency details
- Verify supported cryptographic algorithms and key sizes
- Confirm protocol compatibility specifications
- Review independent security audit reports
Independent Security Audit Verification
Third-party security audits represent the gold standard for confirming perfect forward secrecy implementation quality.
Leading providers regularly publish comprehensive audit results from reputable firms.
Audit evaluation criteria:
- Audits should specifically examine cryptographic implementations
- Look for detailed technical findings rather than summary statements
- Verify auditor credentials and reputation in cybersecurity field
- Check audit recency and regular update schedules
- Confirm audit scope includes key management procedures
Technical Support Evaluation
Professional VPN services provide detailed explanations of perfect forward secrecy implementation when questioned directly.
Support quality indicates overall technical competence and security knowledge.
Support assessment factors:
- Clear explanations of key exchange algorithms used
- Specific details about key rotation schedules and triggers
- Knowledge of protocol configurations and security features
- Ability to discuss technical implementation without marketing deflection
- Professional responses demonstrating genuine security expertise
Leading VPN Providers with Verified Perfect Forward Secrecy
ExpressVPN’s Advanced Implementation
ExpressVPN implements perfect forward secrecy across all protocols with automatic key refresh every 15 minutes during extended sessions and post-quantum cryptography support.
ExpressVPN features:
- ECDHE key exchanges with AES-256-GCM encryption
- Lightway protocol includes perfect forward secrecy by default
- New keys generated during network changes and reconnections
- Multiple independent security audits confirming implementation
- Detailed technical documentation available publicly
ProtonVPN’s Privacy-First Approach
ProtonVPN provides perfect forward secrecy through OpenVPN and WireGuard protocols with Switzerland-based jurisdiction and verified no-logs policy for comprehensive protection.
ProtonVPN advantages:
- Secure Core architecture with multi-hop perfect forward secrecy
- Open-source applications enable implementation verification
- Each connection segment protected by independent keys
- Perfect forward secrecy standard across all service tiers
- Transparent security practices with regular audit publications
NordVPN’s Protocol Diversity
NordVPN offers perfect forward secrecy through NordLynx protocol and OpenVPN connections with 3072-bit Diffie-Hellman groups for enhanced cryptographic strength.
NordVPN implementation:
- Double VPN feature uses independent ephemeral keys per hop
- Multiple protocol options all supporting perfect forward secrecy
- Regular third-party audits confirming security implementation
- Extensive server network with consistent security standards
- Integration with specialty servers maintaining perfect forward secrecy
Mullvad’s Transparent Security
Mullvad supports perfect forward secrecy through WireGuard and OpenVPN with comprehensive technical documentation and anonymous account systems.
Mullvad transparency features:
- Detailed key rotation schedule documentation
- Open-source applications for implementation verification
- Anonymous payment options including cash acceptance
- Complete technical specification publishing
- Regular security audit reports with detailed findings
Perfect Forward Secrecy Integration with Other Security Features
Perfect forward secrecy operates as one component of comprehensive VPN security rather than a standalone solution. Understanding how it integrates with other essential features helps users evaluate complete protection packages.
Synergy with No-Logs Policies
Perfect forward secrecy protects data during transmission while strict no-logs policies ensure VPN providers don’t store information about user activities.
These features address different threat vectors and both remain necessary for complete privacy protection. Even with verified no-logs policies, perfect forward secrecy provides additional protection against forced key disclosure, government surveillance programs, and scenarios where legal pressure might compromise provider cooperation.
Kill Switch Coordination
Perfect forward secrecy secures data during active VPN sessions while kill switches prevent exposure when connections drop unexpectedly.
These complementary technologies ensure continuous protection across all connection states. Modern VPN protocols like UCP and TCP integrate kill switch functionality with perfect forward secrecy to maintain security during network transitions, reconnection attempts, and temporary connection failures.
DNS Protection Integration
Perfect forward secrecy encrypts regular internet traffic while DNS leak protection ensures domain name queries don’t bypass VPN tunnels. Advanced implementations encrypt DNS requests using the same ephemeral keys protecting other traffic.
This integrated approach prevents privacy leaks through multiple potential vectors, ensuring comprehensive protection that covers both content access and the metadata revealing which websites users visit.
Common Implementation Problems and Red Flags
Inadequate Key Rotation
Some VPN providers claim perfect forward secrecy support but implement minimal key rotation that provides limited security benefits. Proper implementation requires automatic refresh systems rather than manual user-triggered key generation.
Key rotation red flags:
- Services generating new keys only upon manual reconnection
- Providers without documented automatic refresh policies
- Key rotation intervals exceeding 60 minutes during active sessions
- Lack of key generation during network transitions
- Absence of technical specifications about rotation triggers
Protocol Compatibility Issues
Perfect forward secrecy requires specific protocol configurations that providers may implement incorrectly or inconsistently. Marketing claims don’t guarantee proper technical implementation.
Protocol verification requirements:
- OpenVPN must include proper ECDHE configuration
- Generic protocol support doesn’t ensure perfect forward secrecy
- Provider transparency about specific algorithm choices
- Technical documentation detailing implementation methods
- Independent audit confirmation of protocol configurations
Performance Optimization Sacrifices
Budget providers sometimes disable perfect forward secrecy features to reduce computational loads and improve connection speeds, sacrificing long-term security for marginal performance gains.
Performance-related warning signs:
- Optional perfect forward secrecy that can be disabled
- Default configurations without ephemeral key support
- Marketing emphasis on speed over security features
- Lack of investment in hardware acceleration for cryptographic operations
- Cost-cutting approaches that compromise essential security features
Future Evolution of Perfect Forward Secrecy Technology
Post-Quantum Cryptography Integration
Researchers are developing quantum-resistant algorithms for perfect forward secrecy implementations that will withstand future quantum computing capabilities.
These post-quantum protocols will replace current elliptic curve methods vulnerable to quantum attacks. Early implementations of quantum-resistant perfect forward secrecy are entering testing phases, with widespread deployment anticipated within the next decade as quantum computing threats become more imminent.
Enhanced Automation and Verification
Future VPN clients may include built-in tools for automatically verifying perfect forward secrecy implementation quality, providing users confidence in their security without requiring technical expertise or manual verification processes.
These verification systems will continuously monitor key exchange processes and alert users if perfect forward secrecy protection becomes compromised through configuration changes or security incidents.
Integration with Emerging Technologies
Perfect forward secrecy will likely integrate with emerging privacy technologies like decentralized VPN networks, blockchain-based authentication systems, and advanced traffic obfuscation methods to provide comprehensive protection against evolving surveillance capabilities.
Selecting VPNs with Reliable Perfect Forward Secrecy
Protocol Support Requirements
Choose VPN services supporting modern protocols like WireGuard or properly configured OpenVPN with verified ECDHE implementations.
Older protocols without ephemeral key support cannot provide authentic perfect forward secrecy regardless of provider marketing claims.
Avoid services offering only PPTP, basic L2TP, or proprietary protocols without independent security audits confirming perfect forward secrecy implementation quality.
Provider Transparency Standards
Select providers publishing detailed technical documentation about cryptographic implementations, key rotation policies, and security audit results.
Transparency about specific algorithms and configuration details indicates professional security management. Companies providing vague security descriptions or refusing to discuss implementation specifics may lack genuine perfect forward secrecy or attempt to hide inadequate implementations behind marketing language.
Audit and Compliance Verification
Prioritize VPN providers undergoing regular independent security audits from reputable firms like PwC, Deloitte, or specialized cybersecurity companies.
These audits should specifically examine perfect forward secrecy implementation rather than general security practices.
Look for providers publishing complete audit reports rather than summary statements, as detailed technical findings enable independent evaluation of security claim accuracy.
Additional Security Feature Integration
Choose services integrating perfect forward secrecy with complementary security features like verified no-logs policies, automatic kill switches, DNS leak protection, and multi-factor authentication for account access.
白标 VPN 解决方案 incorporating perfect forward secrecy can provide enterprise-level security for business applications requiring long-term confidentiality guarantees and regulatory compliance.
Performance Considerations and Real-World Impact
Computational Overhead Reality
Perfect forward secrecy requires additional processing power for ephemeral key generation during connection establishment. Modern devices and optimized implementations minimize this impact to negligible levels, typically adding only milliseconds to connection times.
The computational cost proves worthwhile for the substantial security benefits, particularly as processor capabilities continue advancing while cryptographic algorithm efficiency improves through ongoing optimization research.
Mobile Device Battery Impact
Smartphone and tablet users often worry about perfect forward secrecy affecting battery life through increased cryptographic processing. However, modern mobile processors handle ephemeral key calculations efficiently with minimal power consumption impact.
Battery usage from perfect forward secrecy remains far less significant than factors like screen brightness, cellular signal strength, or background application activity.
Network Performance Optimization
VPN providers must balance security and performance when implementing perfect forward secrecy across thousands of simultaneous user connections.
Advanced server hardware and optimized software architectures enable strong encryption without degrading connection speeds.
Leading providers invest in specialized cryptographic acceleration hardware that processes perfect forward secrecy calculations efficiently while maintaining high-speed connections for streaming, gaming, and large file transfers.
Common Misconceptions and Security Limitations
Protection Scope Understanding
Perfect forward secrecy protects against specific threats related to key compromise but cannot prevent all possible security vulnerabilities.
It provides no protection against malware infections, social engineering attacks, or real-time man-in-the-middle attacks during active sessions.
Users should understand that perfect forward secrecy represents one important component of comprehensive security rather than a complete privacy solution addressing all potential threats.
Performance Impact Myths
Many users avoid perfect forward secrecy believing it significantly degrades VPN performance. Modern implementations cause minimal connection delays, with optimization techniques reducing overhead to levels unnoticeable during typical internet usage.
The security benefits substantially outweigh minor performance considerations for users prioritizing long-term privacy protection over marginal speed improvements.
Universal Implementation Assumptions
Not all VPN providers implement perfect forward secrecy equally, with significant variations in key rotation frequency, algorithm selection, and overall security quality between different services.
Users should verify specific implementation details rather than assuming equivalent protection across providers claiming perfect forward secrecy support.
Choosing the Right Perfect Forward Secrecy VPN
Essential Verification Steps
Research potential VPN providers through multiple sources including technical documentation, independent security audits, and user community discussions focusing on implementation quality rather than marketing claims.
Contact customer support with specific technical questions about key exchange algorithms, rotation schedules, and protocol configurations to evaluate their actual security knowledge and implementation quality.
Red Flags to Avoid
Avoid providers unable to explain their perfect forward secrecy implementation, offering to disable the feature for performance, or claiming support without specifying technical details about algorithms and key management procedures.
Services with histories of security incidents, vague privacy policies, or reluctance to undergo independent audits may indicate inadequate perfect forward secrecy implementation or broader security management problems.
Integration with Privacy Needs
Consider how perfect forward secrecy fits within your broader privacy requirements, including jurisdiction preferences, logging policies, payment anonymity options, and additional security features necessary for your specific use cases.
Balance perfect forward secrecy implementation quality with other factors like server network coverage, streaming compatibility, and pricing to find optimal solutions for your individual security and usability needs.
包起来
Perfect forward secrecy protects your VPN privacy against both current and future threats by creating unique encryption keys that vanish after each session.
This technology ensures that stolen server keys cannot decrypt your historical browsing data, making it essential for long-term digital privacy protection.
When combined with no-logs policies and kill switches, perfect forward secrecy provides comprehensive security against multiple threat vectors.
As quantum computing advances, this feature becomes increasingly vital for maintaining privacy protection against technological breakthroughs that could compromise traditional encryption methods.
常见问题解答
Perfect forward secrecy provides significant protection against future quantum computing threats by ensuring today’s encrypted traffic cannot be decrypted with tomorrow’s advanced computing power. Since session keys are permanently destroyed after each connection, quantum computers cannot retroactively break your historical communications even if they eventually crack current encryption algorithms.
Regular VPN encryption often reuses the same master key across multiple sessions, creating vulnerability if that key gets compromised. Perfect forward secrecy generates unique, temporary keys for each session that cannot decrypt other sessions even if discovered by attackers, providing session isolation that traditional encryption lacks.
Advanced users can analyze VPN connections using network monitoring tools like Wireshark to examine key exchange processes, though this requires significant technical expertise. Most users should rely on provider technical documentation, independent security audit reports, and detailed customer support inquiries to verify proper implementation.
Some budget VPN providers skip perfect forward secrecy implementation to reduce server computational costs and technical complexity. The additional processing requirements and configuration management represent operational expenses that cost-focused providers may avoid despite the significant security benefits for users.
Yes, perfect forward secrecy generates completely new encryption keys each time you reconnect to your VPN, whether due to network changes, manual disconnection, or automatic reconnection after connectivity issues. Each new connection establishes fresh cryptographic protection independent of previous sessions.
![Ultimate White Label VPN Business Guide 2026 [Cost & ROI]](https://symlexvpn.com/wp-content/uploads/2026/01/Ultimate-White-Label-VPN-Business-Guide-2025-Cost-ROI_2-376x114.webp)




